
Take your Cybersecurity Pulse™ before unknown risk becomes real exposure.
Assess, Prioritize, Remediate, Repeat…
You don’t know your risks until you fully assess them.
We provide assessments of current state, awareness and compliance training, remediation plans and implementation support to reduce risks.
We serve Non-Profits/Charities, Public Sector & Private Sector Businesses
Is the Cybersecurity Pulse™ right for you?
Your CyberSecurity Pulse™
Fact: most executive teams and voluntary board members are unaware if their organization complies with their operating agreements or if all cybersecurity threats are mitigated. Cybersecurity Pulse™ will give you this information
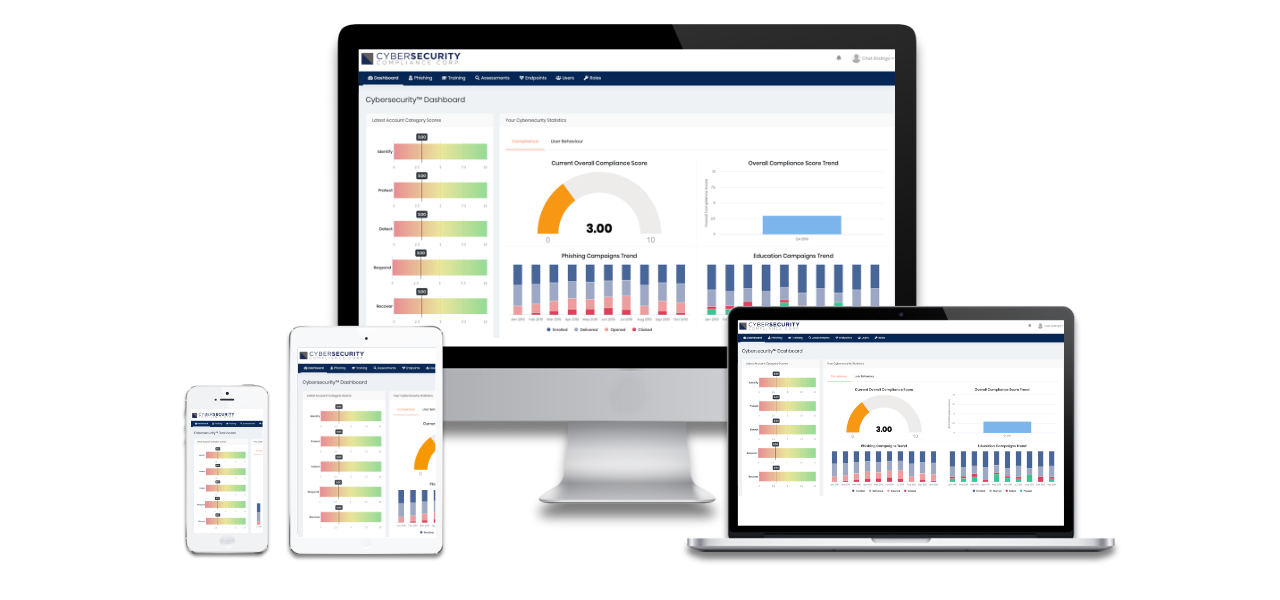
Cybersecurity Pulse™ brings best-in-class education and monitoring tools together to provide a one-stop view of your organization’s cybersecurity environment.
Through our proprietary dashboard interface, share your organization’s cybersecurity compliance progress with your executive team and board of directors with real-time, view-only access to a personalized dashboard, your Cybersecurity Pulse™.
What You Get:
- An unbiased third-party assessment of your cybersecurity environment specifically tailored to Executives and Board Members
- Assessment is delivered via an online dashboard that is easily accessible, always up-to-date, and can be refreshed anytime
- This makes it easier to view, manage, implement and track any changes needed to protect your organization and ensure compliance within your roles and responsibilities as Executives
Mandatory compliance: your supplier or customer contracts includes clauses requiring compliance with minimum or specific cybersecurity, data protection and privacy laws and standards
Insurance compliance: your insurer requires evidence of specific cybersecurity measures or a documented cybersecurity program in accordance with minimum or specific cybersecurity standards
Due diligence compliance: preparing for customer, supplier or potential investor due diligence, requiring documented evidence of a cybersecurity program and compliance with standards
Prioritization, remediation, and monitoring compliance: improving your cybersecurity posture through implementation of policies, practices, procedures, technology, and services
Why choose Cybersecurity Pulse™?

Your solution includes:

In-Class Training
- 1-3 hours
- Professional instructors
- Practical tools and tips

Online Assessment
- Framework-based questionnaire
- Role-based responsibilities
- Real-time updates

Online Education
- Engaging videos
- Customizable frequency
- Prompts and compliance tracking

Simulated Phishing
- Customizable email message
- Variable frequency
- Remedial education

