Solution

Online
Cybersecurity
Assessment

Online
Education

Simulated
Phishing
Campaigns

In-class
Training
Cybersecurity
Pulse ™ Video

From Home
The Cybersecurity Pulse™ Solution
The  Solution
Solution
The Cybersecurity PulseTM solution delivers framework-based assessments with plain-English scoring guidance. Delivered through an intuitive interface and executive dashboard, the Pulse solution includes options for:
- online training modules
- phishing test campaign management
- live webinar or in-person training
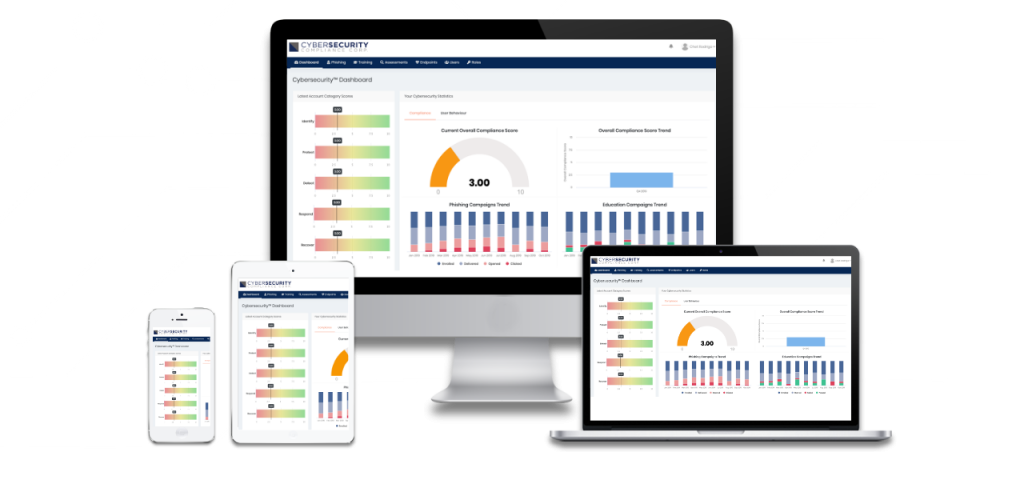

Using a framework-based assessment takes the guesswork out of evaluating or implementing an effective cybersecurity environment. Our assessment provides non-IT executives and board members with a real-time view into the current cybersecurity status of their organization, and allows IT management to establish a roadmap for future improvements and related budget requests that is based on globally-accepted best practices.
What our Clients and Partners are saying about Cybersecurity Pulse™

“As an IT service provider, the Cybersecurity Pulse assessment gives me the comprehensive overview and communication tool I need to help my clients prioritize cybersecurity improvements for their stage and budget. The integration with online education, phishing and endpoint tools reduces the cost of compliance management, and the time it takes to prepare for each management update meeting.” -Jason, Senior IT Specialist, MSP


“There has been a lot of focus on cybersecurity and it was overwhelming trying to decide what initiative to focus on first. Running the Cybersecurity Pulse assessment was easy and comprehensive. Once we had completed our baseline assessment, it was obvious where we needed to focus our attention.” -Pauline, Director of Operations, Wealth Management


“As an IT service provider, the Cybersecurity Pulse assessment gives me the comprehensive overview and communication tool I need to help my clients prioritize cybersecurity improvements for their stage and budget. The integration with online education, phishing and endpoint tools reduces the cost of compliance management, and the time it takes to prepare for each management update meeting.” -Jason, Senior IT Specialist, MSP

“Jeff is highly knowledgable about cybersecurity and how it pertains to business owners and their employees. His presentations are educational and well put together. Jeff is able to engage the crowd so everyone learns something they can apply directly to their everyday behaviours in the workplace. The in-class education session definitely made our employees more cyber-aware and we are making changes right away to protect us and our data. We made notes on how to move forward and make additional changes in the future.” -Diane, Co-Founder & President, Recruitment

“There has been a lot of focus on cybersecurity and it was overwhleming trying to decide what initiative to focus on first. Running the Cybersecurity Pulse assessment was easy and comprehensive. Once we had completed our baseline assessment, it was obvious where we needed to focus our attention.” -Pauline, Director of Operations, Wealth Management
Features
| Solution Features | Pulse | Pulse+ |
| Cybersecurity Pulse Assessments and Executive Dashboard | ||
| One-on-one administrator walk-through | ||
| Dedicated onboarding support for three months | ||
| Role-based deployment | ||
| Plain-English scoring | ||
| User-friendly executive dashboard | ||
| Initial assessment results review | 1 hour | 2 hours |
| Annual education or prioritization session | 1 hour | 2 hours |
| – your choice of staff education, board education or prioritization session | ||
| Multiple frameworks per site | ||
| Compliance evidence upload and management | ||
| Cost per site (business unit) | Contact for pricing | Contact for pricing |
| Education and Phishing Campaign Management | ||
| Online educational videos | ||
| Simulated phishing emails | ||
| “Set and forget” education and phishing campaign administration | ||
| Campaign results displayed on executive dashboard | ||
| Cost per enrolled user1 | Contact for pricing | Contact for pricing |
| Additional Services | ||
| In Class Education/Webinar | Custom pricing | Custom pricing |
| Remediation consulting | Custom pricing | Custom pricing |

ONLINE
CYBERSECURITY
ASSESSMENT
Assessment
- User-friendly, role-based assessments with plain English scoring
- Full results review and prioritization discussion with seasoned IT management and risk professionals
- Easily understood, complete picture of your cybersecurity environment
- Budget and stage-appropriate roadmap for improvements over time
- Dynamic tracking of improvements over time
Education
User error accounts for up to 90% of successful breaches. With computer-based training, you can significantly change the odds. Ongoing user training ensures your clients are kept up to date on the latest methods of attack, so they stay on track and out of the headlines. Succinct, easily consumed, interactive courses increase end users’ attentiveness, as well as the overall effectiveness of cybersecurity education programs.
Our education module lets you launch effective online education programs in minutes.

ONLINE
EDUCATION

IN-CLASS
TRAINING
In-Class Training
In-class education sessions are a great way to demonstrate company commitment to a culture of cybersecurity and to introduce the topic to resources across the organization.
Our instructors have several decades of training experience in the technology and governance areas, and bring both a level of subject-matter expertise and real-world experience to sessions designed to inform and educate across all levels and functions in the organization.


 Solution
Solution